
Generate Wildcard Let's Encrypt Certificate with nginx and Namecheap
Namecheap offers SSL certificates support but it costs around $10 for the first year, where as there are free solutions to getting SSL for your website like Let’s Encrypt using Certbot. So, that’s why after 1 year with namecheap’s PositiveSSL I tried switching to the free Certbot solution.
In this tutorial we will cover how to generate a
wildcard Let’s Encrypt certificate using Namecheap as the
DNS and nginx as the web server on Ubuntu (22.04.3 for me).
Since there is no certbot plugin for namecheap, the method is more manual.
| Category | Required |
|---|---|
| System | Ubuntu in this tutorial |
| Software | snapd, OpenSSH - both are preinstalled on Ubuntu |
| Access | Root privileges - user root or with sudo |
If you have any Certbot packages installed using an OS package manager like apt, dnf, or yum, you should remove them before installing the Certbot snap to ensure that when you run the command certbot the snap is used rather than the installation from your OS package manager:
$ sudo apt-get remove certbot
$ sudo snap install --classic certbot
certbot 2.7.4 from Certbot Project (certbot-eff✓) installed
Make sure that the certbot command can be run with this command:
$ sudo ln -s /snap/bin/certbot /usr/bin/certbot
Now we have to manually generate the certificate which requires a lot of steps.
First, because we’re trying to get a wildcard cert, we need to add a certain TXT DNS record value to our Namecheap domain.
We can obtain a value for the TXT record from Let’s Encrypt with:
| |
And replace example.com with your own domain (xxlsteve.net for me).
Here, -d "*.example.com" -d "example.com" assures that all subdomains will be allowed HTTPS, but also the root domain, example.com. If for instance you don’t need
TLS/SSL for example.com for example because you access your site via www.example.com, you can simply put: -d *.example.com.
After entering your email address, it should give you a value to add to a TXT record under the name:
_acme-challenge.example.com.
Go to your namecheap domain’s advanced DNS settings, and under host records, add a new TXT record.
Add _acme-challenge for the Host value and the given value to Value.
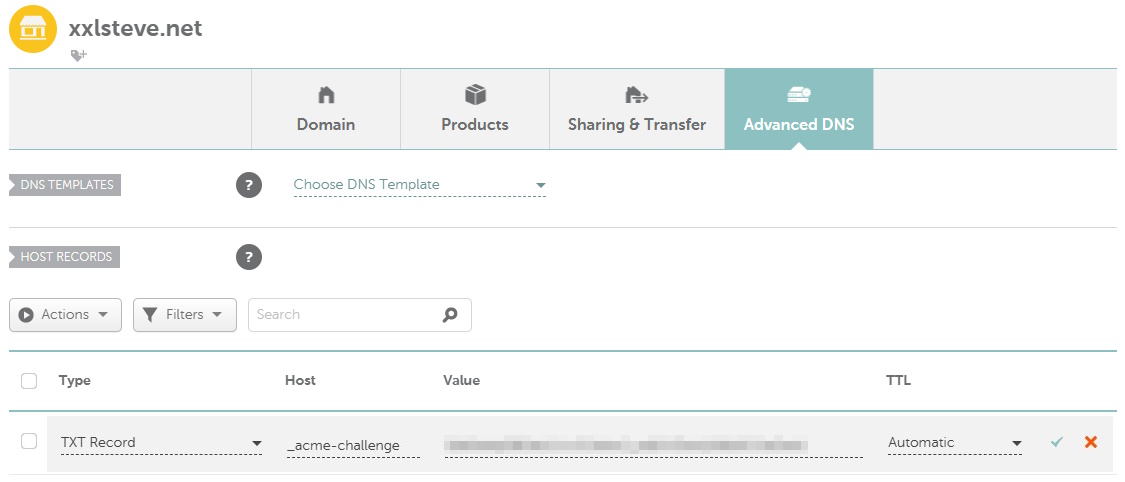
Now, wait until Namecheap has synced the new record (might take a minute). To test if it’s done, you can run this command on a command prompt:
nslookup -type=TXT _acme-challenge.example.com
(Of course, replace example.com with your domain)
If it succeeds it should return the following:
Server: 192.XXX.XXX.XXX
Address: 192.XXX.XXX.XXX
Non-authoritative answer:
_acme-challenge.example.com text =
"XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX"
Alternatively, you can use this online tool:
https://toolbox.googleapps.com/apps/dig/#TXT/_acme-challenge.example.com (replace example.com at the end).
Since it succeeded, you can now press Enter back in Ubuntu to continue the certificate creation process.
When that’s done, fullchain.pem and privkey.pem will be generated most likely in /etc/letsencrypt/live.
Command response and steps
| |
Now you just need to include the newly generated certificate in your nginx website’s configuration. The most basic (but not secure!) implementation would be these 2 lines in your server block:
| |
The certificate needs renewal every 90 days, though preferably every 60.
While the default Cerbot installation methods provide automatic renewal, the manual installation needs to be combined with an authentication hook script via --manual-auth-hook. That is, running the original command would instead be:
| |
This will run the authenticator.sh script, attempt the validation, and then run the cleanup.sh script.
However, these scripts need access to Namecheap’s API to perform the otherwise manually done task of validation. But the criteria to qualify for API access is the following:
“Account balance of $50+, 20+ domains in your account, or purchases totaling $50+ within the last 2 years.”
…which is probably not the case for you.
Since automatic renewal is not possible because of Namecheap API criteria, the only option left is the manual way. That means running the same command every 60 to 90 days, and therefore repeating the task of adding a TXT record to your domain, etc.
Personally, Google calendar notifies me every 90 days to renew the certificate by running the command from Run Certbot command.